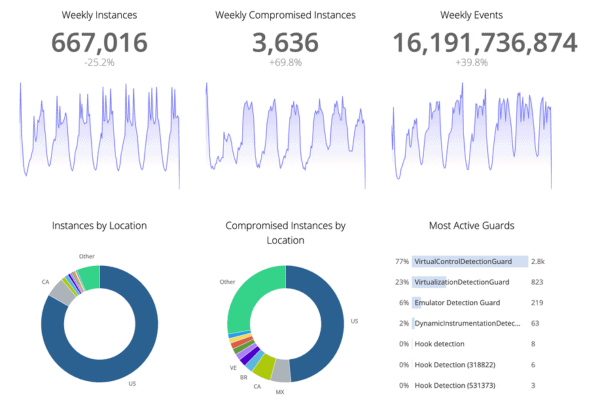
What is Threat Monitoring and the Role of Threat Intelligence
Threat monitoring is essential for maintaining the security and integrity of information systems in an era where cyber threats are increasingly sophisticated and pervasive. This proactive security measure allows organizations to detect and respond to potential security incidents.
Threat monitoring is a critical cybersecurity practice that involves the continuous observation and analysis of network environments and endpoints to detect, identify, and respond to potential security threats. This proactive approach utilizes a combination of technology, processes, and expertise to safeguard information systems from both known and emerging threats. By integrating various security tools such as intrusion detection systems, malware analysis, and behavioral analytics, threat monitoring can identify unusual or malicious activities that may otherwise go unnoticed. This enables organizations to respond swiftly to potential threats, minimizing damage and preventing breaches. Effective threat monitoring also involves continuous refinement of security measures based on the latest threat intelligence and evolving attack methods, ensuring that the defense mechanisms are always a step ahead of potential attackers. Through vigilant monitoring and rapid response strategies, organizations can maintain a robust security posture and protect their critical assets from cyber incidents.
Importance of Threat Monitoring
Threat monitoring is essential for maintaining the security and integrity of information systems in an era where cyber threats are increasingly sophisticated and pervasive. This proactive security measure allows organizations to detect and respond to potential security incidents before they escalate into damaging breaches. By continuously analyzing network behavior, communications, and endpoints, threat monitoring helps identify suspicious activities and anomalies that could indicate a cyber attack or internal misuse. This early detection is crucial for limiting the impact of threats, reducing downtime, and protecting sensitive data. Furthermore, effective threat monitoring provides valuable insights into threat patterns and vulnerabilities, enabling organizations to refine their security strategies and enhance their defensive measures. Overall, threat monitoring is fundamental not only for immediate threat detection and response but also for long-term resilience and compliance with regulatory requirements, ensuring that organizations can safeguard their operations and reputation against the evolving landscape of cyber risks.
Understanding Threat Landscape: Types of threats
The cyber threat landscape is vast and diverse, encompassing a range of malicious activities designed to harm or exploit digital systems. Viruses and worms are some of the oldest forms of malware, designed to infect, replicate, and spread to other computers, often corrupting data or taking over system resources. **Ransomware** is a particularly disruptive type of malware that encrypts a victim’s data, then demands payment for the decryption key. **Phishing attacks** involve deceiving individuals into providing sensitive information by masquerading as a trustworthy entity in electronic communications. Spyware collects information about an individual or organization without their knowledge, leading to privacy violations and potential data breaches. Distributed Denial of Service (DDoS) attacks aim to overwhelm systems, servers, or networks with a flood of Internet traffic, disrupting services for legitimate users. Advanced Persistent Threats (APTs) are stealthy and continuous computer hacking processes, often orchestrated by persons targeting a specific entity. Crypt-jacking is another emerging threat where hackers use someone else’s computing resources to mine cryptocurrency. Reverse engineering is a technique used by threat actors to understand how applications work in order to discover how the app communicates with the server (in order to perpetrate attacks on the server) or to otherwise manipulate the app in order to get it to do something it was not meant to do. Together, these threats pose significant challenges to cybersecurity professionals tasked with defending digital infrastructures in an ever-evolving threat environment.
Emerging Threats to Watch Out For
Cybersecurity professionals should stay vigilant against several emerging threats as technology evolves. Artificial Intelligence (AI) and machine learning are being leveraged to create more sophisticated phishing and social engineering attacks that are harder to detect, while also making it easier for threat actors to analyze applications and reverse engineer them. Supply chain attacks have become prevalent, where attackers compromise trusted software sources to distribute malware widely. The Internet of Things (IoT) expands the attack surface with many connected devices often lacking robust security, making them easy targets for breaches. 5G technology, while increasing network efficiency, also introduces new vulnerabilities due to its decentralized nature and the vast number of connected devices. Ransomware continues to evolve with ransomware-as-a-service platforms making it easier for non-technical criminals to launch attacks. Reverse engineering is a technique used in the cyber threat landscape primarily for analyzing malware and discovering paths to servers in software and hardware systems. By deconstructing software and understanding how it operates, cybersecurity professionals can identify how clients communicate with servers, and anticipate and mitigate potential attack vectors. Keeping abreast of these reverse engineering and other threats is crucial for cybersecurity professionals to develop effective defense strategies.
Role of Threat Intelligence in Threat Monitoring
Defining Threat Intelligence
Threat intelligence plays a pivotal role in threat monitoring by providing actionable information about emerging or existing threats that can affect an organization. This intelligence encompasses detailed analyses of threat actors, their tactics, techniques, and procedures (TTPs), and indicators of compromise (IOCs) that help security teams identify and mitigate potential risks. By leveraging threat intelligence, organizations can prioritize their security responses, enhance their defensive mechanisms, and tailor their threat monitoring strategies to be more proactive and targeted. This results in a more robust defense posture that aligns real-time security information with organizational risk management goals.
Utilizing Threat Intelligence in Monitoring
Utilizing threat intelligence in monitoring involves integrating real-time intelligence feeds into security systems to enhance the detection and analysis of threats. By embedding this intelligence into tools like protection blueprints, SIEM systems, firewalls, and intrusion detection systems, organizations can automate the process of identifying and responding to indicators of compromise. This allows security teams to swiftly detect unusual activity patterns that match known tactics, techniques, and procedures of threat actors. Additionally, threat intelligence can be used to adjust security policies and implement appropriate defenses, such as individual guards or protections, based on the severity and relevance of the intelligence, ensuring that the organization’s security measures are always aligned with the latest threat landscape. This proactive approach not only speeds up response times but also improves the overall efficiency and effectiveness of the threat monitoring process.
Threat Monitoring Techniques and Tools
Network Security Monitoring
Network Security Monitoring (NSM) tools defend computer networks. These tools allow organizations to detect, analyze, and respond to both ongoing and potential security threats and incidents. NSM tools continuously collect network data, such as traffic logs, packets, and flows, and analyze this data to identify suspicious activities and anomalies that may indicate a security breach. By providing real-time visibility into network operations, these tools enable security analysts to track threat behaviors, assess their impact, and respond promptly to mitigate risks. Additionally, NSM tools often include features like threat intelligence integration, alert systems, and automated response capabilities, which help streamline the monitoring process and enhance the overall security posture of an organization. Through comprehensive monitoring and analysis, NSM tools play a crucial role in protecting network integrity and safeguarding sensitive data from cyber threats.
Endpoint Threat Monitoring
Endpoint threat monitoring, especially focused on client applications is a critical component of a comprehensive cybersecurity strategy. This process involves continuously analyzing client applications running on computers, smartphones, and browsers, to detect and respond to malicious activities targeting client applications. By employing real-time monitoring tools and techniques, such as dynamic instrumentation detection and checksum guards, organizations can identify suspicious application behaviors, such as unauthorized data access, unusual network connections, or unexpected changes in file integrity. This enables IT security teams to quickly isolate affected applications and mitigate threats before they can spread or cause significant damage. Endpoint threat monitoring ensures that client applications remain secure from exploitation, maintaining both the integrity of the devices and the confidentiality of the data they contain.
Top Threat Monitoring Tools
RSA Netwitness: A comprehensive network threat monitoring tool that RSA claims can monitor the entire IT enterrprise infrastructure. Includes threat hunting and detection capabilities, customizable dashboards, and uses machine learning to detect potential threats and generate real-time alerts automatically.
Snort: An open-source tool that is in many of the largest enterprise security operations centers worldwide. Snort analyzes network traffic and identifies a wide range of threats such as malware, spyware, and remote exploits. Snort is considered a “rule-based” system that works largely on the basis of anomaly detection.
Splunk Enterprise Security: Perhaps the best known of the security information and event managers (SIEMs) that monitors the entire IT infrastructure with a focus on network traffic. Splunk uses machine learning to identify threats and provide threat mitigations. It also offers an advanced correlation engine plus threat hunting capabilities.
Digital.ai App Aware: One of the only application threat hunting products on the market that focuses solely applications that are outside of the enterprise IT infrastructure or firewall. App Aware monitors attacks on application through “guards” or protections that are built-into apps as part of the application build process. App Aware is typically integrated with the SIEMs and threat monitoring tools described above in order to augment the threat monitoring of apps inside the enterprise firewall.
Implementing Threat Monitoring in Your Organization
Implementing threat monitoring in an organization involves a series of strategic steps that enhance security posture. Initially, it is essential to conduct a thorough risk assessment to identify the organization’s most critical assets — inclusive of the applications that the organization makes available to both employees and customers — and the potential threats they face. Based on this assessment, the next step is to select appropriate threat monitoring tools and technologies, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and client application monitoring tools, that align with the organization’s specific needs. Following the selection of tools, deploying and configuring these solutions to accurately monitor network traffic, system logs, and endpoint applications is crucial. Training IT staff to manage these systems and interpret the alerts they generate is another critical step, ensuring that the team can respond swiftly and effectively to detected threats. Finally, continuously updating and refining the threat detection, mitigation, and monitoring processes and tools in response to evolving threats and changing organizational requirements will ensure that the monitoring efforts remain effective and relevant. Through these steps, an organization can establish a robust threat monitoring framework that provides ongoing protection against potential security threats.
Effective threat monitoring is essential for maintaining a secure organization that can respond promptly to cyber threats and minimize potential damage. This process requires a robust framework that integrates advanced monitoring tools, such as intrusion detection systems and security information event management systems, with real-time threat intelligence to anticipate and identify potential security incidents. It involves continuous assessment and updating of security measures to address emerging threats and adapting the threat monitoring strategy based on organizational changes and evolving risk landscapes. Properly training and equipping security teams to interpret and act on monitoring data is crucial, ensuring that they can quickly isolate and mitigate threats. Ultimately, successful threat monitoring is characterized by its proactive stance, enabling an organization to detect threats early, respond effectively, and maintain operational integrity in the face of the dynamic and ever-present nature of cyber threats.